
NetGuard: Securing Network Environment Using Integrated OpenVPN, Pi-Hole, and IDS on Raspberry Pi | SpringerLink

install snort on raspberry pi – BriarIDS – A home intrusion detection system (IDS) solution for the Raspberry PI.

how do i install snort on raspberry pi – BriarIDS – A home intrusion detection system (IDS) solution for the Raspberry PI.

Electronics | Free Full-Text | Forensic Analysis on Internet of Things (IoT) Device Using Machine-to-Machine (M2M) Framework
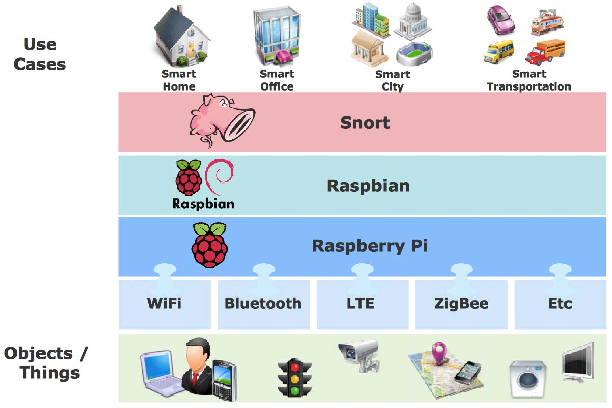
Figure 1 from RPiDS: Raspberry Pi IDS — A Fruitful Intrusion Detection System for IoT | Semantic Scholar
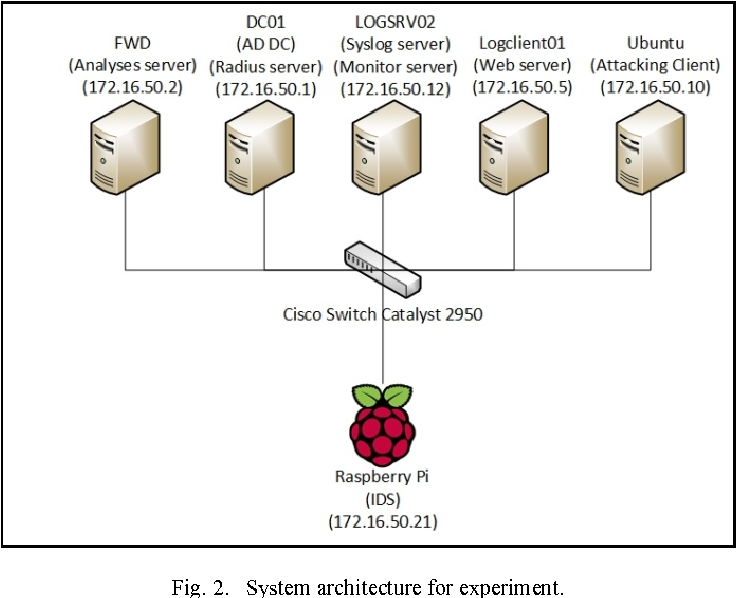

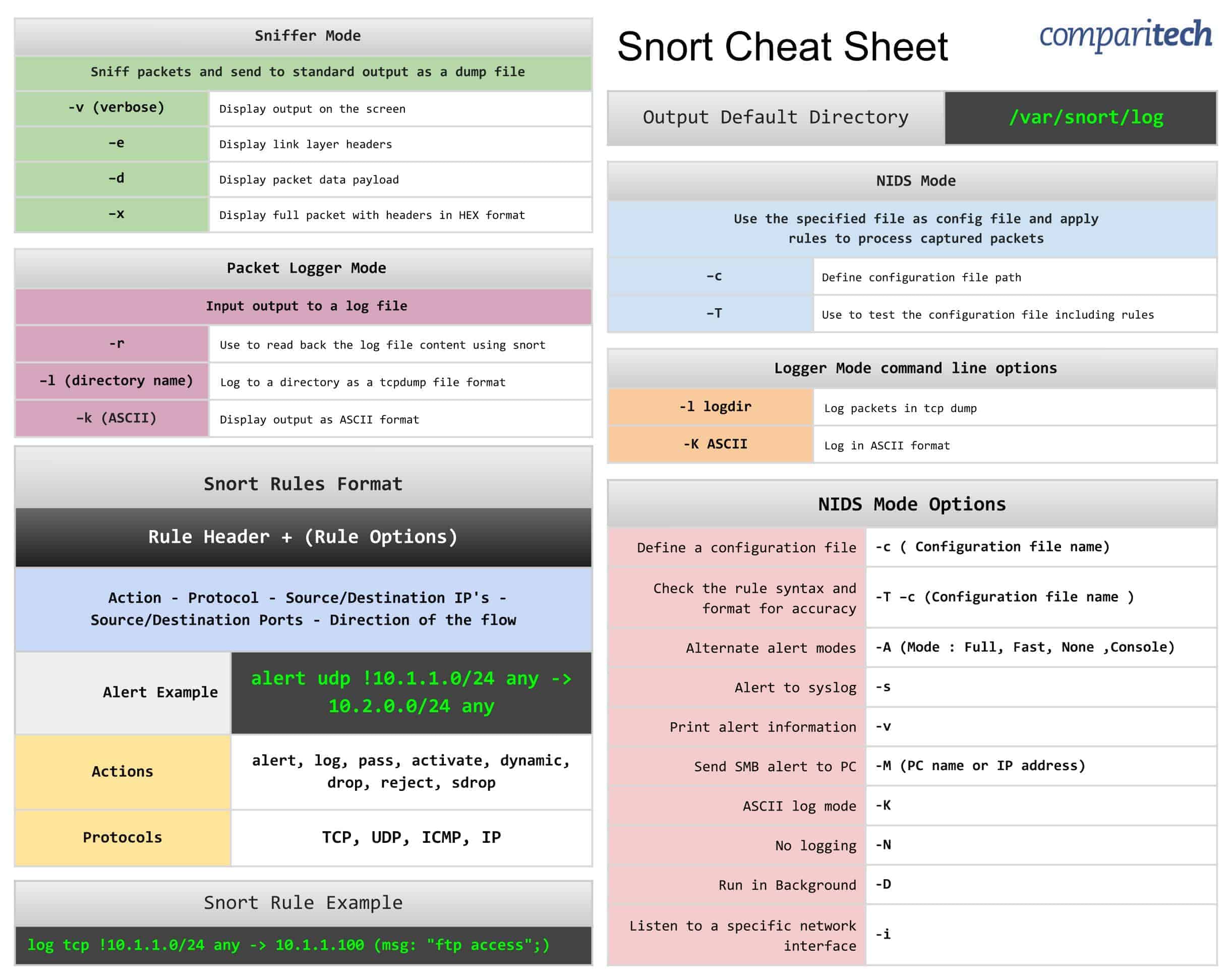


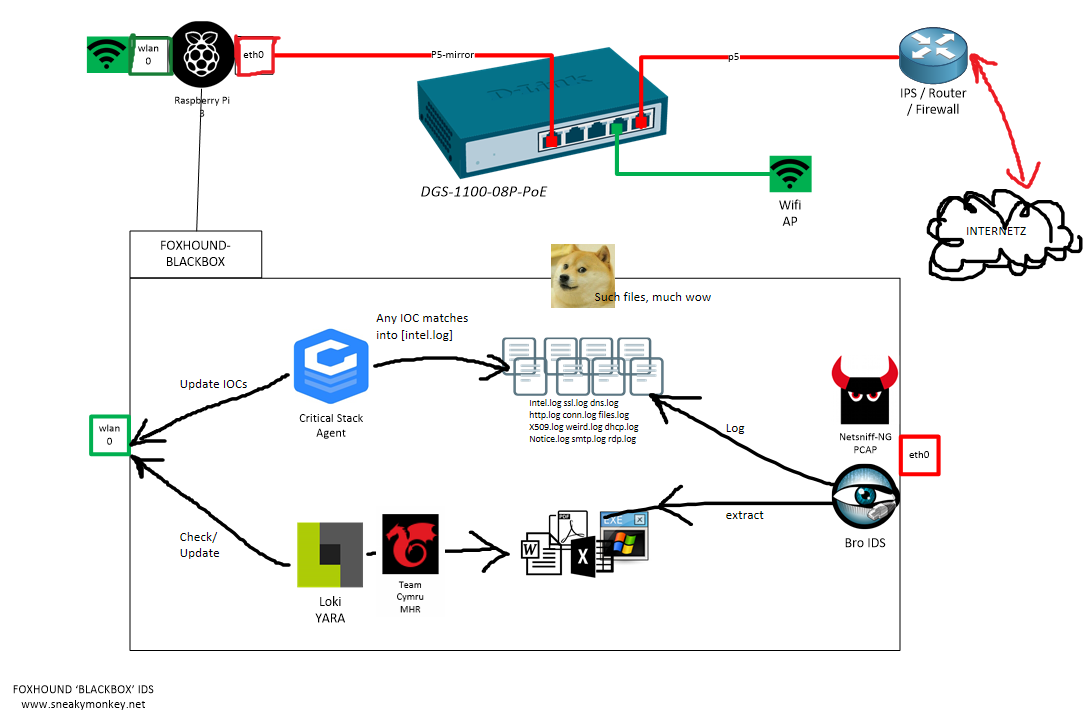


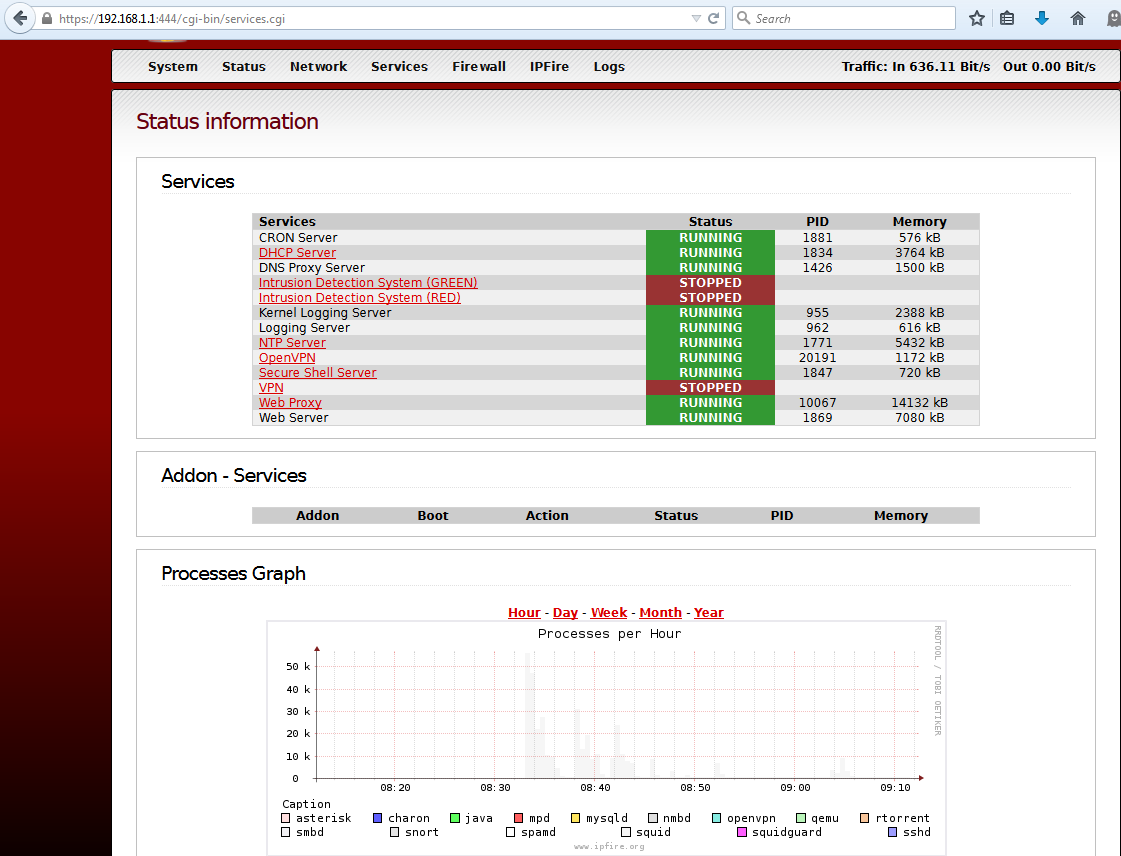

![Configuring Snort IDS [FREE COURSE CONTENT] Configuring Snort IDS [FREE COURSE CONTENT]](https://i.ytimg.com/vi/lWlnCbeGYzg/maxresdefault.jpg)